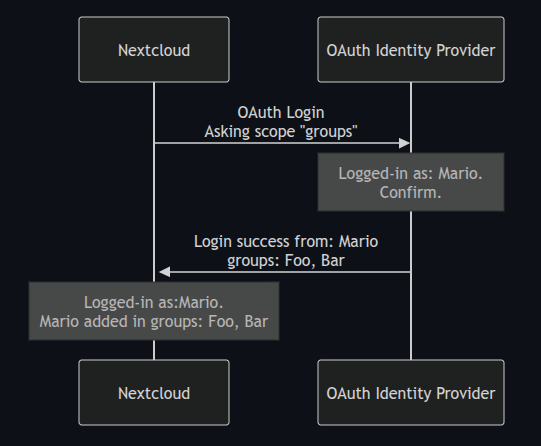
Here is the mockup pic for adding Oauth Scopes in Nextcloud, but how should it actually be implemented?
from kiol@lemmy.world to selfhosted@lemmy.world on 20 Aug 23:13
https://lemmy.world/post/34748472
from kiol@lemmy.world to selfhosted@lemmy.world on 20 Aug 23:13
https://lemmy.world/post/34748472
Specific suggestions appreciated! Here is admin doc related section and more info on scopes. Here is github issue.
threaded - newest
oauth.net/articles/authentication/
That aside, why is nextcloud asking for scopes from remote API in the diagram? What is drawn on the diagram has little to do with OAuth scopes, but rather looks like an attempt to wrap ACL repository access into a new vocabulary.
Scopes issued by the OAuth authorization server can be hidden entirely. The issuer doesn’t hold any obligation to share them with authorized party since they are dedicated for internal use and can be propagated via invisible or opaque means.
I really can’t figure out what’s going on with that diagram.
Thank you for answering this person, it amazes me how little people know of oauth, and it’s not a new tech.
The email address scope is commonly used as a common identifyer for linking accounts.
Thanks, this helped me better understand what is going on. Tried to formulate a response: github.com/nextcloud/server/issues/26233#issuecom…
I’d probably add that for something like nextcloud granted scopes can be an „orthogonal”–for the lack of a better word–subset of requested scopes.
The set of requestable scopes has to be defined by the system itself, not its specific configuration. E.g. „files:manage”, „talk:manage”, „mail:read” are all general capabilities the system offers.
However, as a user I can have a local configuration that adds granularity to the grants I issue. E.g.: „files:manage in specific folders” or „mail:read for specific domains or groups only” are user trust statements that fit into the capability matrix but add an additional and preferably invisible layer of access control.
It’s a fairly rare feature in the wild and is a potential UX pitfall, but it can be useful as an advanced option on the grant page, or as a separate access control for issued grants.
OpenID via keycloak
I think you are getting confused there, the doc you are linking to are for linking an external application to your Nextcloud account, whereas your diagram seems to be connecting Nextcloud to an external IDP.
You may be wanting : apps.nextcloud.com/apps/oidc_login or apps.nextcloud.com/apps/user_saml