from notquitenothing@sh.itjust.works to selfhosted@lemmy.world on 30 Nov 2025 16:14
https://sh.itjust.works/post/50748401
VoidAuth is Single Sign-On for Your Self-Hosted Universe! 🐈⬛🔒
This release includes Multi-Factor Authentication (MFA) Support through TOTP Authenticators! There are other features in this release, like a migration from pug to ejs for email notification templates and quality of life improvements like a built-in container healthcheck, navigation between some admin pages, and reducing the character minimum for usernames to just three letters (sorry ted); but MFA is the big one! Users can enable MFA on their accounts to require an Authenticator or Passkey during sign in, and admins can add MFA requirements to groups, OIDC Clients, and ProxyAuth Domains to require users to setup and use MFA in specific scenarios.
Since the last major release functionality has also been added to migrate your database between SQLite and Postgres, check out the docs! Here is the release notes:
Features 🚀
- MFA Support Through TOTP Authenticators and Passkeys
- MFA_REQUIRED Environment Variable and MFA Requirement Option for Groups, Clients, and ProxyAuth Domains
- Email Templates Migrated to EJS, Defaults Templates Are Now Re-Written on Start
- Navigation Between Admin Pages for User and Group
Fixes 🔧
- Change Username and Name Character Requirements (3 Character Minimum)
Chores 🧹
- Added Dockerfile Healthcheck
- Update Dependencies
Docs 📖
- Update OIDC-Guides.md by @Cherryblue in github.com/voidauth/voidauth/pull/162
Screenshots
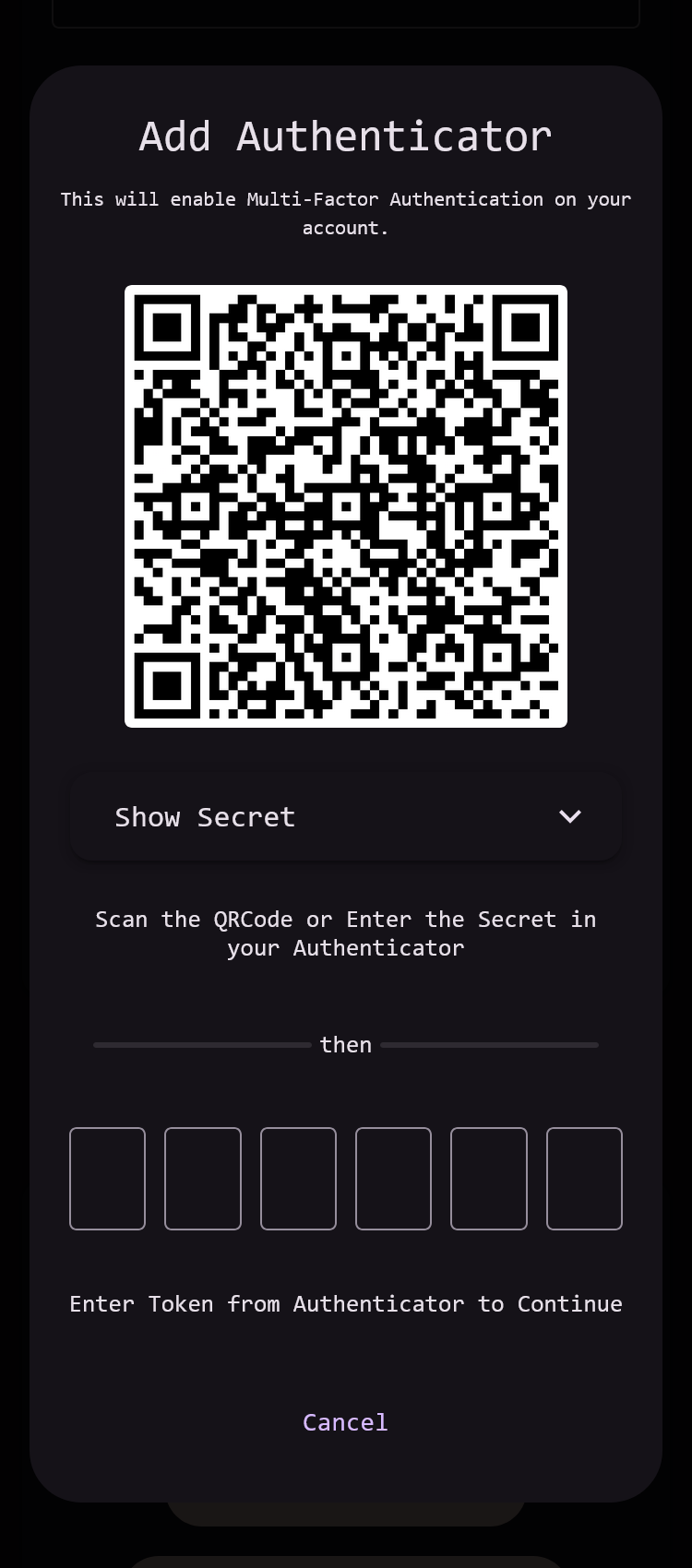
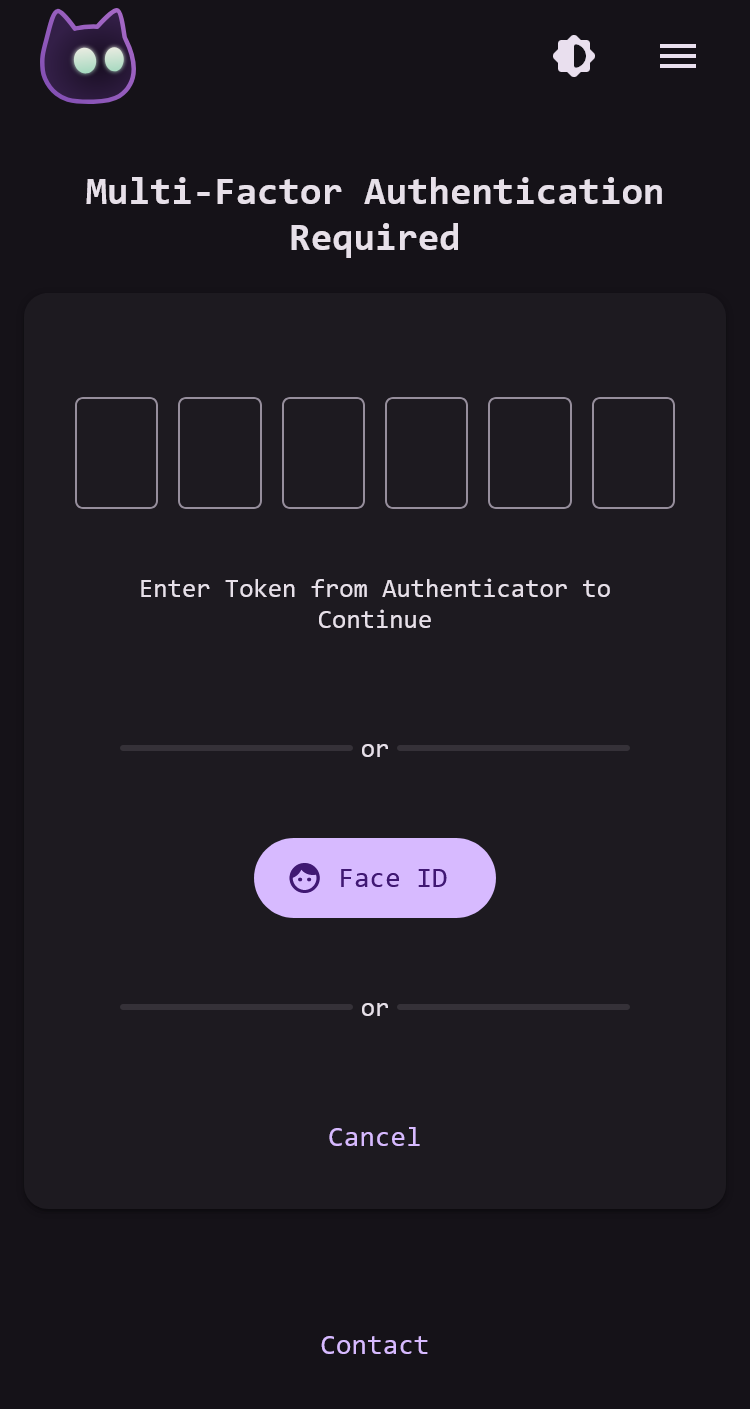
This release includes the first outside contribution to the project as well as the first sponsor! The VoidAuth repository also blew up a bit over the week, going from ~200 to ~600 stars on GitHub. I have no idea why, but seems pretty cool! Thank you to everyone who engages with VoidAuth in any fashion, you are all greatly appreciated 😊
threaded - newest
This looks less intimidating than Authentik. Any guides on getting it set up with any common self-hosted stuff?
I would recommend checking out the Getting Started page in the docs, which I realize can be a lot! Once you have an initial instance running (you can always change environment variables later to suite your needs) and have logged in with the initial admin username and password that appear in the logs on first start, you can check out the Admin Guides section in the docs sidebar. There you should be able to see pages relating to OIDC Setup (including for specific apps) and other topics. If you set up OIDC on a new app that doesn’t yet have documentation, PRs with updates to the documentation are welcome! If you have any questions you can feel free to ask in the repo issues/discussions and I will try to help out 😊
It’s beautiful. It took me under an hour to implement. I never got authentik or authelia working, and this is all in one container.
Is there any feature comparison between this and pocket-id? I think they fill a very similar gap, but I’m tempted to try VoidAuth, mainly cause the aesthetic is way cuter imo
There is no direct feature comparison between VoidAuth and pocket-id (‘comparison is the thief of joy’ after all). At least one major difference is that pocket-id does not allow users to sign in with a password since passkey-only accounts are one of their design decisions, and VoidAuth does not support LDAP integration while pocket-id does. My main motivation in creating VoidAuth was to fill gaps in my own user experience while using SSO, previously I ran Authelia+LLDAP (which is still an excellent combo) but found the setup lacking in some common use-cases and devoid of an Admin Interface.
I am glad you like the interface and logo, it is inspired by my own black cat who right at this very moment is yelling for pets 😹