from new_otters_raft@piefed.ca to selfhosted@lemmy.world on 20 Feb 18:00
https://piefed.ca/c/selfhosted/p/538455/tailscale-services-ga-app-aware-connectivity-with-more-control
This should be excellent for selfhosters that have all their services in one VM. I haven’t tried this myself, but I think this means you can:
- you can create memorable links instead of memorizing port numbers: jellyfin.foo-bar.ts.net
- share one service from a machine instead of all of them in a more intuitive way
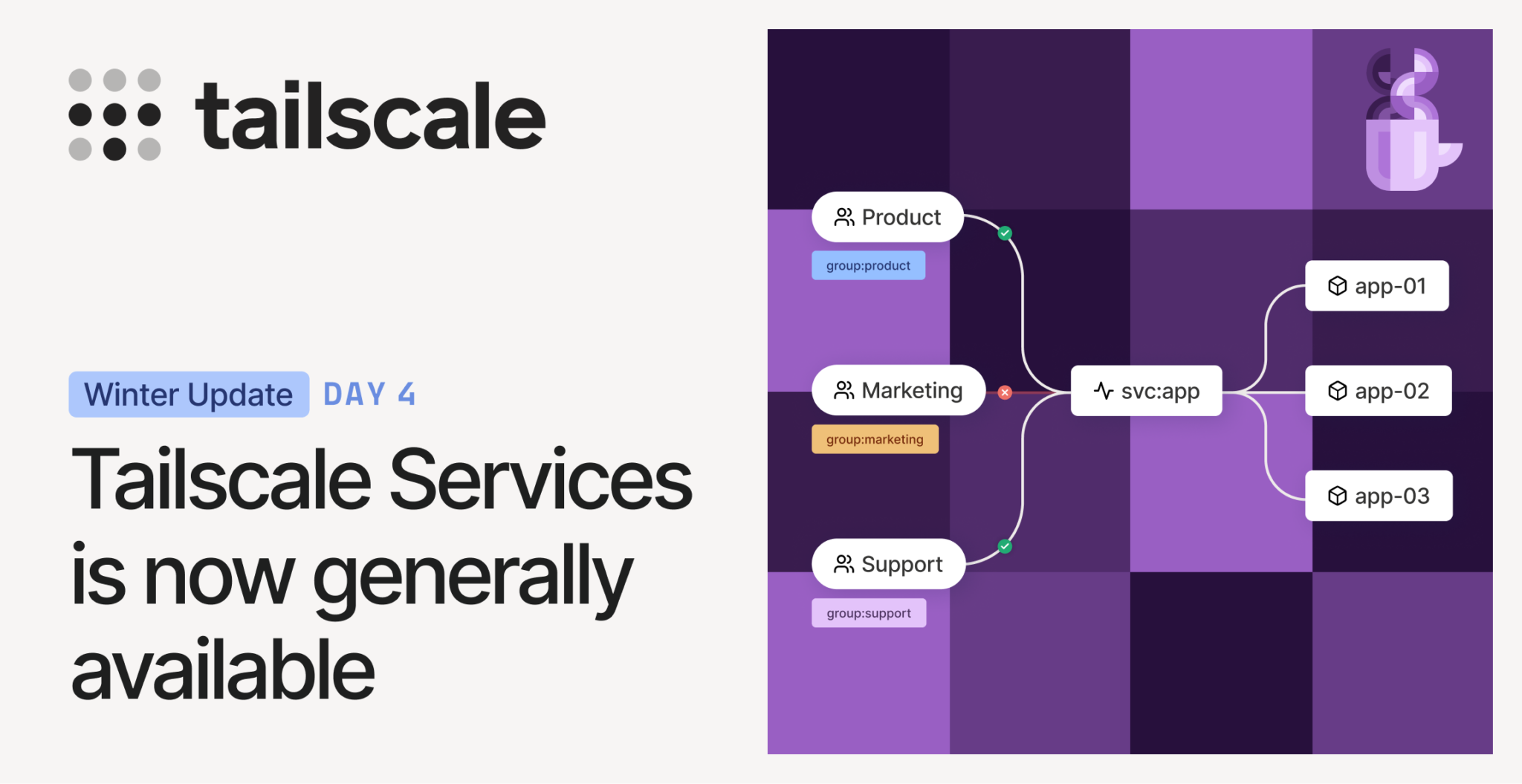
If you’re new to Tailscale Services, it lets you publish internal resources like databases, APIs, and web servers as named services in your tailnet, using stable MagicDNS names. Rather than connecting to individual machines, teams connect to logical services that automatically route traffic to healthy, available backends across your infrastructure. This decoupling makes migrations, scaling, and high availability far easier, without reconfiguring clients, rewriting access policies, or standing up load balancers. Our documentation has details on use cases, requirements, and implementation.
threaded - newest
While this is great, especially for smaller self-hosters, as a setup gets more and more dependent on Tailscale, one should think about self-hosting Headscale, and therefore not being over-reliant on services not offered by it. I’m in that boat and I haven’t done the Headscale migration yet.
I did it about 8 months ago… it just works like black magic. It’s a “fire and forget” VPN, but SSO is a must in my opinion; otherwise, key exchange is too tedious.
You’re talking about Headscale right?
Yes… sry wasn’t clear about that…
Can you share what components are you using for SSO, UI, etc.?
Not OP but I use headscale and have it configured using Authentik for SSO. Works flawlessly once its up and running. I also use headplane for the UI. It has SSO integration as well which makes everything a breeze.
Edit: Forgot to mention, all running in docker with traefik as the reverse proxy.
Never got warm with all the UIs available. But things change very fast on that front. For me it looks like that they only differ by the time it takes to provide support for the newest headscale version. Just take the one supporting yours :) For SSO , the OIDC provider from Nextcloud is working as good as any other. Having some kind of static IP also helps but the headscale server runs on HTTPS port plus some optional ones (not sure if I remember correctly) dynamic dns should be ok as well.
What is it about Tailscale that is giving you heartburn? I am over reliant on my ISP. Without them, selfhosting would be rather bland.
Ownership, size and profit growth strategy. My ISP is a massively profitable poorly regulated oligopoly. The deal there is clear - they’re already charging as much as the market can afford. They aren’t providing a free service today that they’ll have to monetize down the line to compensate for the time operating on VC funding. Tailscale, awesome as it is today, is in my view guaranteed to enshittify over time as they start getting pressed to grow profit. That’s not too much of a problem for me since the clients I use are open source and there’s an alternative open source server. If I used features unavailable in Headscale or were in over my head and unable to self-host Headscale, I might be in a bad time some time down the line.
Would it make you feel better if you paid Tailscale for one of their plans? It’s not like they are just giving away their whole enterprise. It’s fairly trivial for them to give free services, kind of like Cloudflare, Oracle, et al. Reading a bit reveals:
That seems pretty profitable. Enshitification happens. It’s been going on since I was born. If it’s free on the internet, and later it becomes a paid service, then I just find something else that fits. Or pony up the cheapest plan they have, which currently is their Personal Plus @ $5 USD per month. I don’t mind paying for a good service and $5 USD is burger from McDonalds. Extremely well under what most people put into a hobby. Will prices increase? Maybe…everything goes up. Rarely do services and utilities go down in price. When the price points are no longer justifiable, again, I look for something else that fits.
There’s also Netbird, worth checking out.
I’ve heard great things about Netbird. There are all manner of choices. Their team plan @ $5 USD looks rather generous for homelab operation.
That’s one way to look at it. I used to look at paid VC-funded services like that. I no longer do as I’ve observed services I paid good money for get more expensive much faster than inflation and decrease in quality and features at the same time. It’s one reason I self-host many services I used to pay third parties for. I now look to alternatives from the get go and derisk existing dependencies. To be clear - profitability isn’t merely the only problem. The ownership and its profit growth strategy (and expectations) are. Those are not the same in a decades old ISP and a VC-funded startup.
Merely being profitable today isn’t a good predictor for stable prices and function over the long run for VC-funded services. I’m not planning to do major surgery to my setup every few years as yet another service shits the bed. The workstation/server where my self-hosted services run has last been reinstalled in 2014. Most of my config-as-code was written in 2019. I support a few families with this and I aim at maximum stability with minimal maintenance. So I use open source whenever I can and I often pay for development. I only integrated Tailscale in my setup because the clients are open source and because there’s an open source server option.
I’m not saying to people - don’t use Tailscale. In fact I often recommend it to new self-hosters. But I do that because there’s a way out. So here I’m reminding people who care about a way out to check if this feature is escapable. :D
I switched to pangolin and I am amazed how well it works.
Love pangolin. Although I wish internal connections would make more sense
Neat. What would be a good application for App-aware connectivity?
Acronyms, initialisms, abbreviations, contractions, and other phrases which expand to something larger, that I’ve seen in this thread:
6 acronyms in this thread; the most compressed thread commented on today has 10 acronyms.
[Thread #106 for this comm, first seen 20th Feb 2026, 18:41] [FAQ] [Full list] [Contact] [Source code]
jellyfin.foo-bar.ts.netBTW, I’m doing something similar with standard DNS records that point to an internal Tailscale IP. I can go to immich.mydomain.com which only works if Tailscale is active. Let’s Encrypt works too. Obviously the setup isn’t automatic but it’s automateable for more adept self-hosters.