Umami is vulnerable - upgrade immediately
from Mubelotix@jlai.lu to selfhosted@lemmy.world on 09 Dec 13:28
https://jlai.lu/post/29883346
from Mubelotix@jlai.lu to selfhosted@lemmy.world on 09 Dec 13:28
https://jlai.lu/post/29883346
All umami instances have been infected with a persisting crypto miner. Umami was affected by the next.js CVE but quietly released a fix, so most of their users missed it
threaded - newest
Link? Did you discover this yourself? There is no actual info here.
github.com/umami-software/umami/issues/3852
Thank you!
All recently open issues are about this. I was a victim, but I’m not the first and people on reddit have done better investigations than I have. Look for the name of the process at the top
Thanks.
For severe incidents like this, please post the most appropriate link, in this case github.com/umami-software/umami/issues/3852
Admins in self hosted usually don’t have that much experience with real, active compromise and may panic, let’s help them as much as possible.
I will add that Umami itself is not compromised, but vulnerable. That is a somewhat misleading title.
What was the vector? Did you have umami exposed publicly?
Wow I’m glad I happened to see this here. Thank you for the post. I was just thinking about putting all my services behind a VPN too, I think I’m going to go ahead and put that at the top of the list…
I don't think a vpn would help here
.
Yes I re-read the cve, I thought it was an issue with an npm package with a cryptominer
Yeah but Umami is an analytics engine powered by client side tracking. If it was behind a VPN it would be useless.
Unless it was the software package itself that was compromised.
It was not
I don’t know about “all umami instances being infected” but they were certainly all vulnerable.
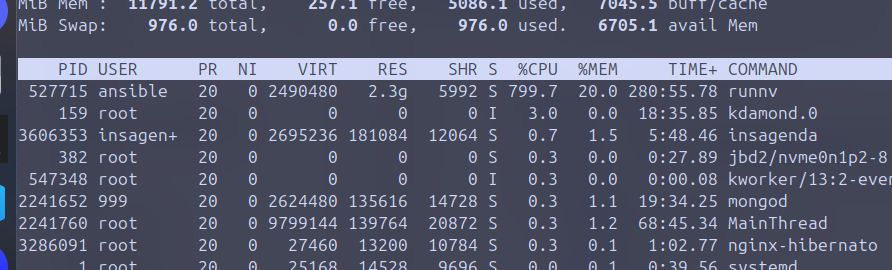
I see it’s running Ansible. That’s an obvious risk.
Source for that claim? Because vulnerable does not mean infected.
Also, I’m kinda glad my instance has been offline for a while now because of database trouble. That was lucky.
Just another day on the job
This could explain why my 4C/8T VPS started hitting 100% CPU usage shortly after boot with like next to nothing else running on it.
Yup, umami was the culprit in my case. Quick update and it’s all running smooth again.